In this article, we’ll configure AWS Identity and Access Management (IAM) to easily use Amazon Sumerian with multiple users. This is especially important for classrooms or trainings. You often don’t want to loose time by having attendees set up and activate their own AWS accounts, including their personal credit cards.
Instead, by setting up sub-users in your account beforehand, you have complete control over the experience and can get started right away. Additionally, it helps with troubleshooting for exercises.
Right now, no ready-made AWS Educate classrooms are available that support Amazon Sumerian. If that changes, the classrooms would be a good alternative, as it gives students their own free AWS credits instead of everything billed to a central account.
Securing Your Account
The first step is making sure you own root account is properly secured. A major part is enabling Multi-Factor Authentication (MFA) for your root account. Especially when working in teams and with source control, it’s an easy-to-make mistake to upload your credentials somewhere; you don’t want others to have full control over your whole AWS account, as this can incur major charges to your credit card. Therefore, it’s best to enable MFA before you continue.
The SMS-based MFA variant is no longer available. Therefore, the best way is using an authenticator app on your phone – like Microsoft Authenticator or Google Authenticator. Both of them handle AWS MFA.
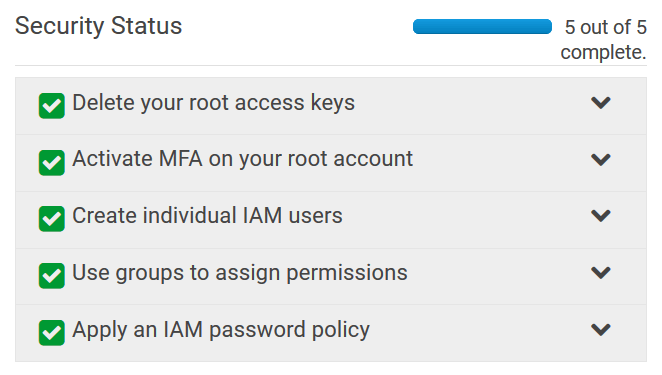
The dashboard of the Identity and Access Management (IAM) console has a nice and brief overview that directly links to the steps required to set up IAM. Make sure you have at least the MFA check box and the IAM password policy checkboxes green before proceeding. Groups and individual IAM users is what we’re setting up next.
IAM Groups
Now, create a group within your account. This is helpful for keeping an eye on the permissions you need for the training, as well as for assigning all users.
From the IAM dashboard, go to Groups and select Create New Group. For the group name, enter the title and date for your course.
The next step is about adding policies. This depends on which services you want to be used within the course. Permissions should obviously neither include user management nor billing administration. In general, give as little permissions as possible.
IAM Managed Policies
The Amazon Sumerian documentation refers to the managed policy for Sumerian. This policy includes access to all services that are internally accessed by Sumerian – e.g., for storage. As it’s a managed policy, you don’t need to care about that, even if Sumerian should require new or different policies in the future.
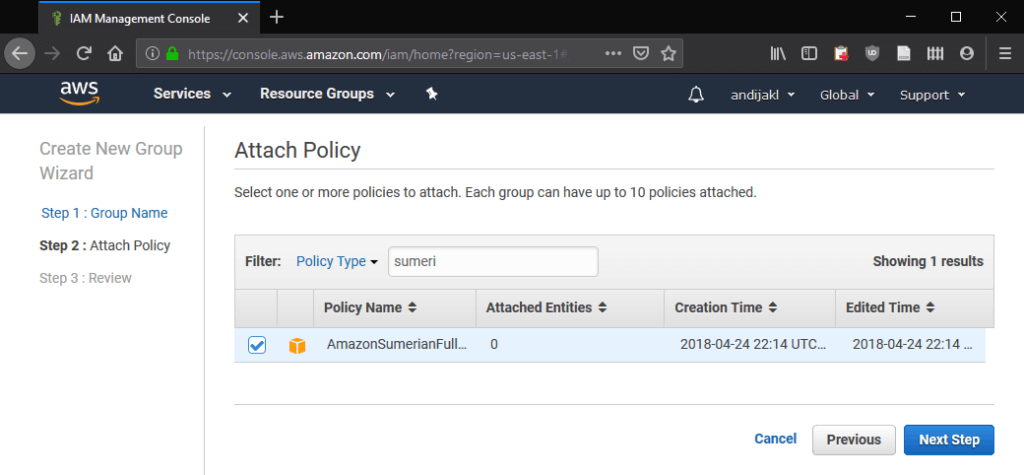
Simply filter for “Sumerian”. The results contain the AmazonSumerianFullAccess managed policy. This is what you need.
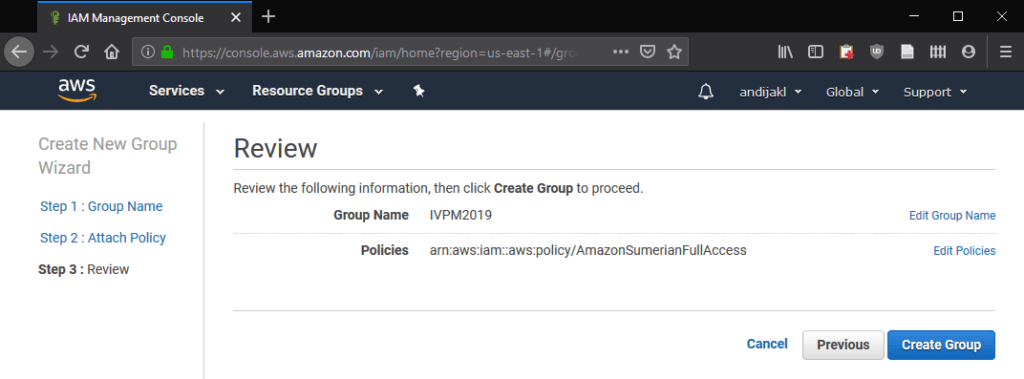
The final step lists the summary of your new group:
IAM Users
After creating the group, the next step is adding users. First, decide whether every student should get their individual user, or if you’d like them to work in teams. In my case, teams are the better choice, as it also allows collaborating on exercises.
From the IAM dashboard, go to Users -> Add User. You can conveniently add multiple users at the same time. For the access type, choose AWS Management Console access. You want your teams to log in and use Sumerian from their browser.
Autogenerated password together with Require password reset is fine if you’re OK with not being able to log in to your team’s accounts yourself later on without resetting the password. A custom password with no required password change might be easier to troubleshoot issues from teams during the course.
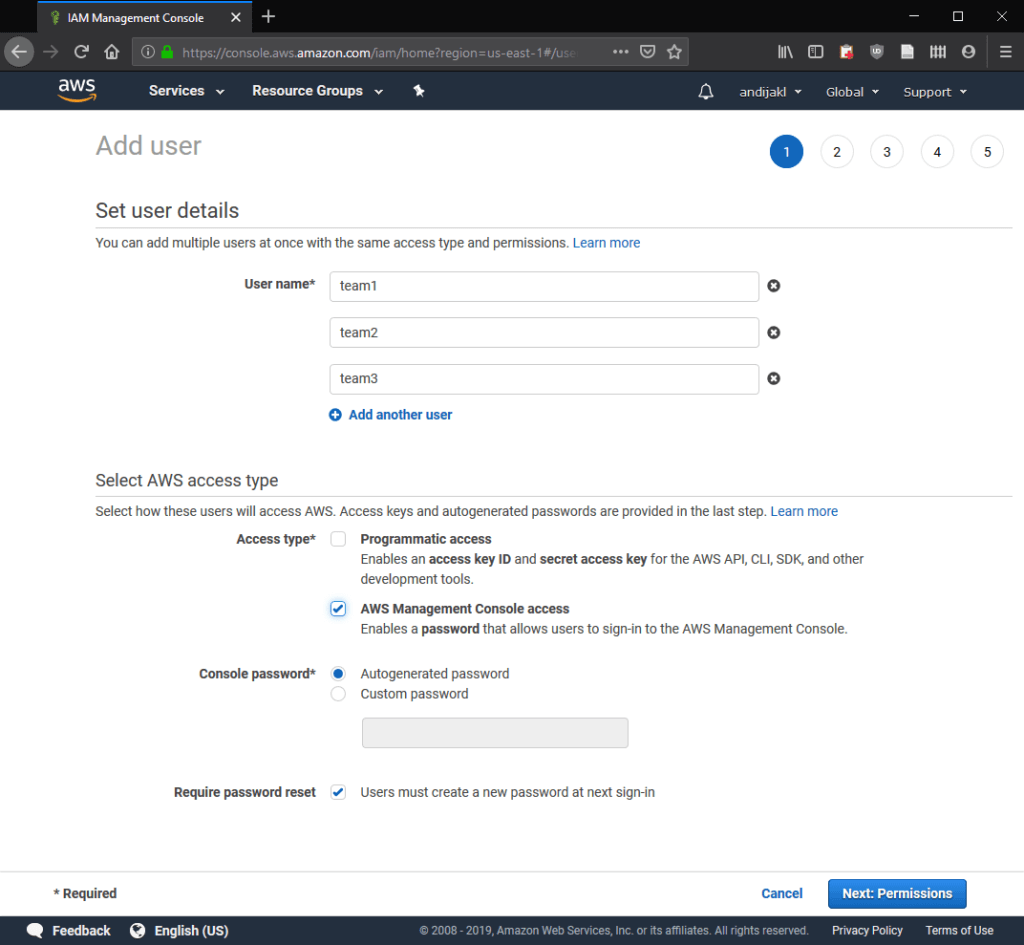
In the next step, add your new users to the group we’ve just created. This also ensures that the users have access to the Sumerian service, as defined by the policy assigned to the group.
You don’t need to assign any tags and can then finalize user creation. On the success page, be sure to note the AWS Management console access URL from the green box. The users in the list are the account names for the log-in. In case you had auto-generated passwords selected, this is also the best chance to retrieve and write down the passwords for each team.

Testing Access
Now, it’s time to test if access works. Open a new private / incognito window in your browser and access the custom console login. Next, access the Sumerian service – it should work fine.
If you created team-users, note that Sumerian doesn’t currently support multiple people from the same account working on the same scene at the same time.
AWS Polly Access: Federated Identities
For using plain Amazon Sumerian, you’re all set. However, the feature where Sumerian really shines are the hosts and their speech features. As such, the Sumerian service needs to access the Polly text-to-speech service internally to convert the test to a sound file.
Again, the Amazon Sumerian Permissions guide contains a brief summary of the required steps. First, go to the Federated Identities page on the Amazon Cognito page. There, create a new identity pool.
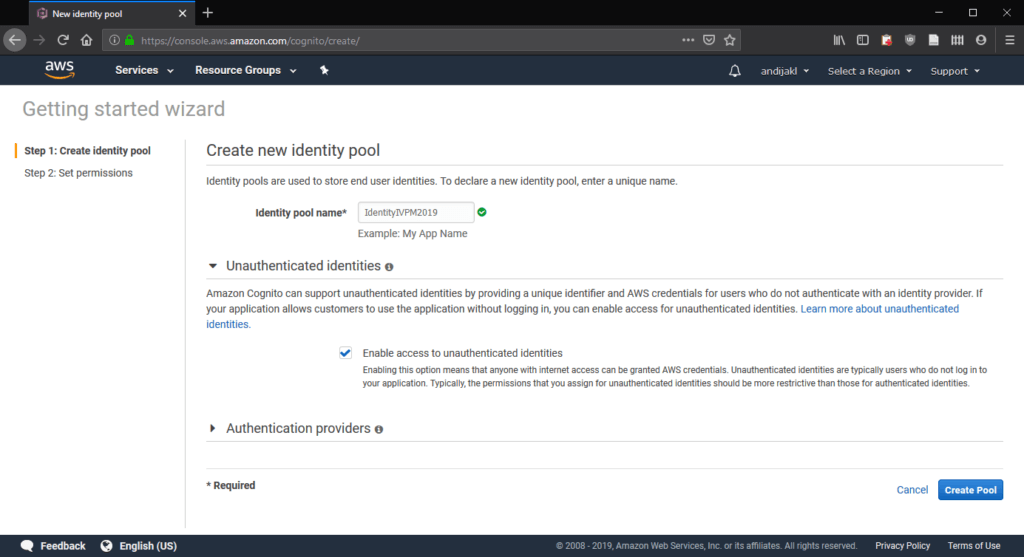
Give it a name and – very important – also check “Enable access to unauthenticated identities”. Amazon Sumerian does not use authentication to access the polly service (yet). Finally, click on “Create Pool”.
Cognito will create two IAM roles: one for authenticated, and another for unauthenticated access. Keep the default values and continue.
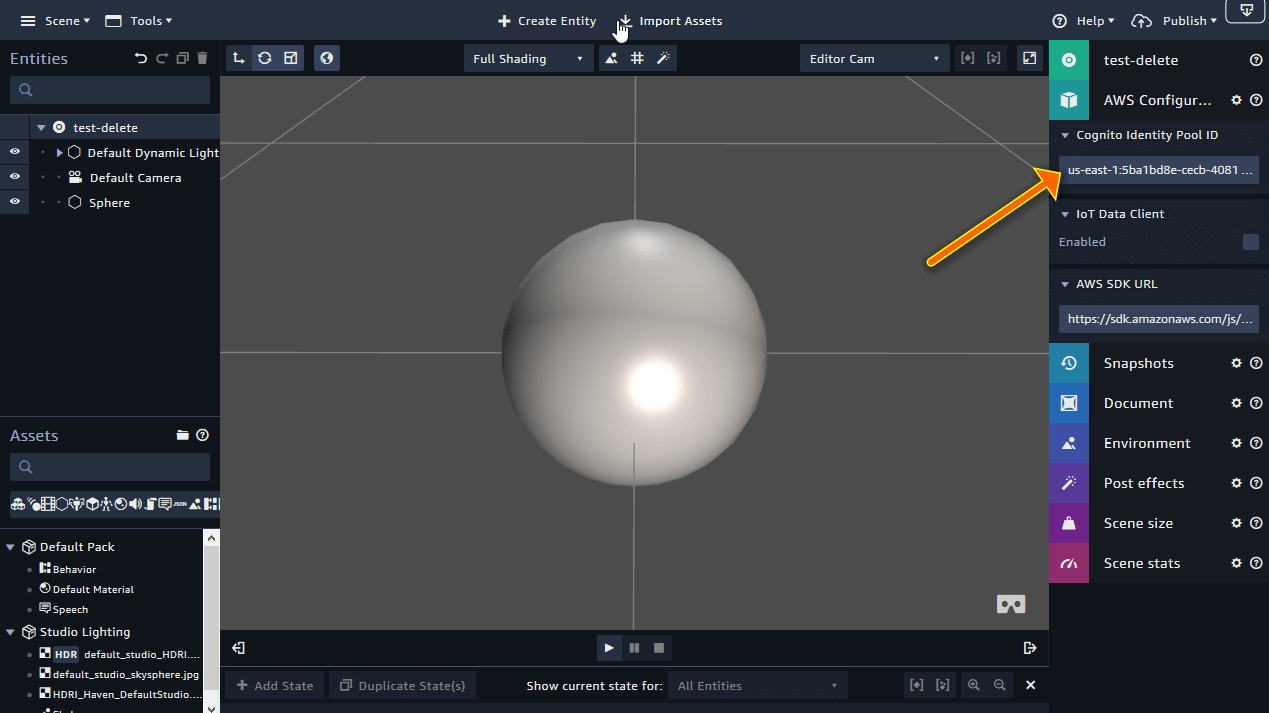
On the summary page, make sure you copy the IdentityPoolId. This is what you’ll need to enter into Sumerian to give it access to speech services. It’s highlighted by the arrow in the screenshot below:
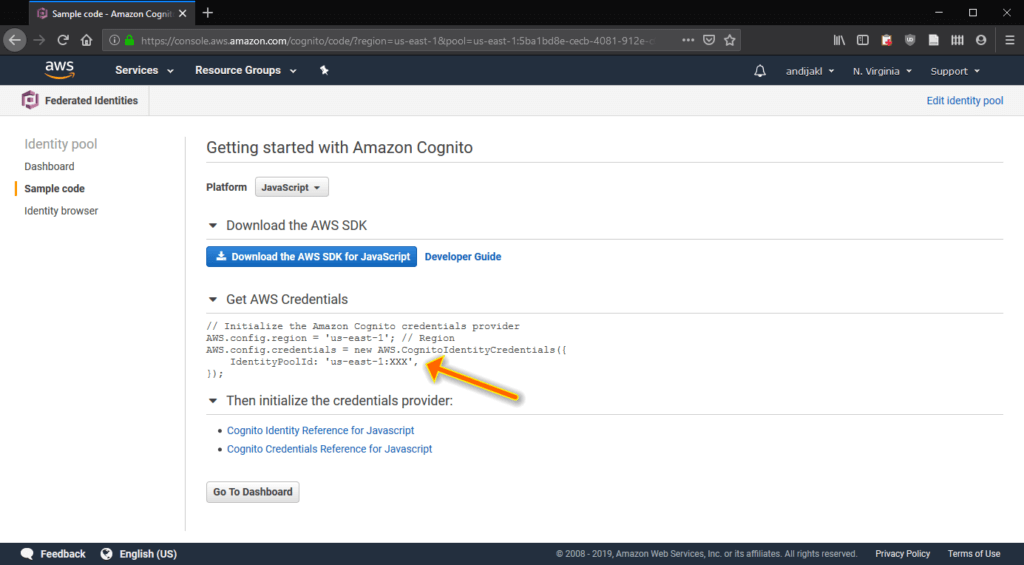
Polly Access for Cognito Role
Go back to the IAM console and access the Roles administration page. There, select the unauthenticated version of the role you just created:
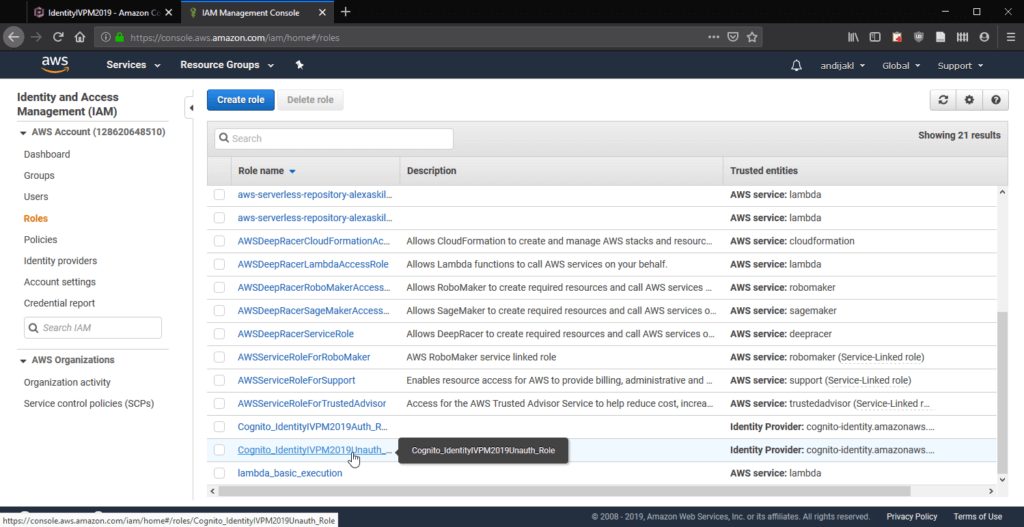
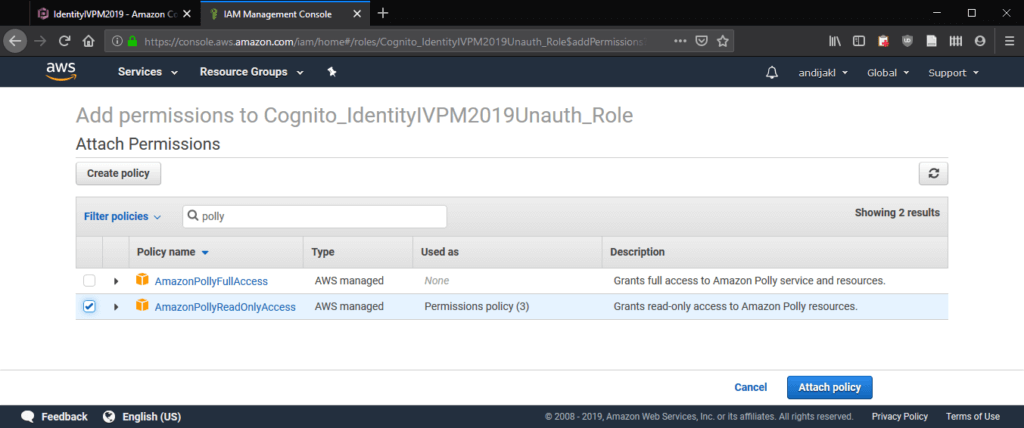
By default, this role already has one inline policy applied. Add the AmazonPollyReadOnlyAccess to it as well. Again, it works fine to just filter for this policy and finally click on Attach policy.
Final Testing
To summarize it, you have created:
- A group to easily assign permissions to the whole classroom. In this case, they have permission to access the Amazon Sumerian service.
- Serveral users for individual students or student teams. These are part of the group.
- A Cognito identity pool that manages access to the Polly text-to-speech service within AWS. The identity pool has two individual roles assigned: for authorized and un-authorized access.
- An un-authorized access role with read-only access to Polly. Sumerian doesn’t currently use authentication, so make sure to keep the identity pool ID secret.
To test, log in to Sumerian with one of the student accounts. Don’t forget to select the region you’d like to work in from the top right corner. Create a small sample scene that uses text-to-speech and add the cognito identity pool ID to the scene properties:
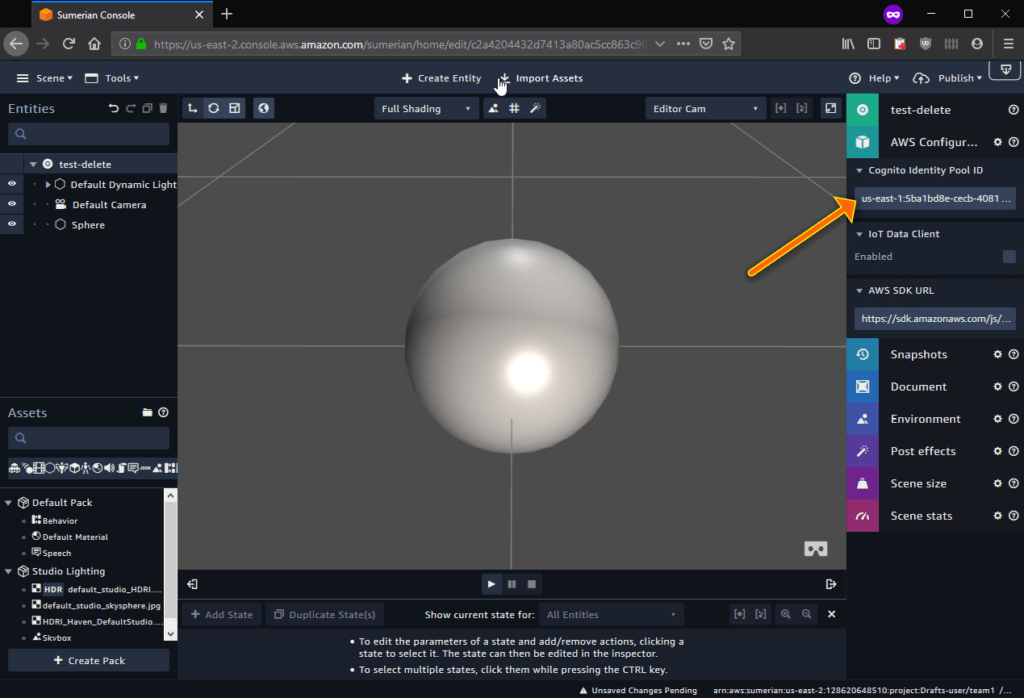
Now, everything should work! All participants can immediately log in and start working with Sumerian. All teams can use the same identity pool ID to access speech services.